vyatta nat设置入门
本文将介绍在vyatta下NAT (Network Address Translation)的类型及配置方式,关于NAT原理,请参考这里。
NOTE: Destination NAT happens first! Meaning that all firewall policies need to be written for POST DNAT operations.(DNAT最先发生,这意味着所有防火墙策略需要由DNAT处理后才可操作。)
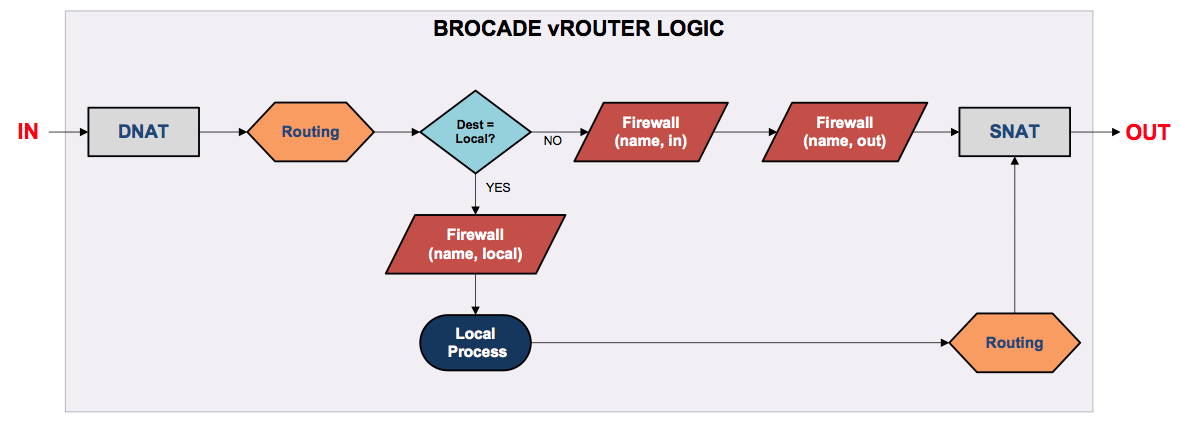
它支持目前主流的三种NAT模式:Source NAT, Destination NAT, and Bi-Directional NAT (Both Source/Destination NAT),下列我们就开始了解它们吧。
There are a couple of points I would like to cover before going into the NAT configurations(在NAT配置中有如下一些要点):
1、Since NAT is a stateful operation, we do not need to configure bi-directional NAT for all configurations. The Brocade vRouter keeps track of the stateful NAT operations using the connection-tracking table.(NAT使用了状态表来跟踪维护此类包的的状态)
2、Unlike routing which will match the most specific entry, NAT operations are processed from top to bottom, with the first successful match used. All other NAT processing will be terminated at that point. Meaning it is important to number your NAT rules accordingly when planning your NAT scheme.(与路由相匹配的最具体的条目不同。NAT是从小到大的处理(规则号),如果最先匹配的那条符合规则的话,后面的规则将会终止处理,所以有必要規划好具体的逻辑并为之编号)
3、All NAT rules on the vRouter include the following parameters:
3.1、Defined traffic to be translated (filters)
3.2、The port-translation address (or the masquerade command if using the vRouter interface IP as the translated address)
3.3、The interface of which to apply the rule. Due to the nature in which the vRouter processes traffic, the translation type will determine the interface on which to apply the rule.
3.3.1、Source NAT – Applied on the outbound interface
3.3.2、Destination NAT – Applied on the inbound interface
4、The direction of the traffic. (Source, Destination, or both)
Source NAT (SNAT):
SNAT is the most common form of NAT. SNAT changes the source address of the packets traversing the vRouter. Typically used in a scenario where you need to translate the internal (RFC1918) addresses to a public routable address.(SNAT是最常见的NAT,SNAT瘵修改vRouter的包的源地址。最典型的场景是公司通过报号上网就是用的此类方式)
# 变量: 描述:
1、Rule Number Number of the SNAT rule. ules will be applied in numerical order.(以数字顺序编号的规则集)
2、Source Address Can be an IP or subnet of IPs.(源地址是ip地址段)
3、Translation Address Can be an IP Address. "masquerade" option uses the vRouter interface IP.(被转换为其它地址,masquerade为最常见)
4、Outbound Interface Interface that traffic will be egressing through.(定义要'出去'的网口)
Here a sample configuration of SNAT using 192.168.148.0/22 as the source, and the eth0 interface IP address as the translated IP:(以下示例用于将192.168.148.0/22这一段ip地址为源,将其转换通过eth0的ip地址出去)
configure
edit nat source rule 10
set source address 192.168.148.0/22
set outbound-interface eth0
set translation address masquerade
commit
save
exit
Destination NAT (DNAT):
DNAT changes the destination address of packets passing through the vRouter. DNAT is typically used when an external host needs to initiate a session with an internal (private) host. For example, translating a static public IP address to two internal server addresses, mapping them by a specific port. For our example, we will use the following parameters:(DNAT改变数据包的目的地址通过vRouter,DNAT时通常使用一个外部主机需要启动一个会话与内部(私有)主机。最常见的用法是将公网内部机器上的服务通过这种nat映射到公网上,让公司外部也可以访问内部这台机器上的服务,就好像这个服务就在公网的ip一样)
1.1.1.1 = Destination address
10.0.0.5 = Web Server (port 80)
10.0.0.10 = SMTP Server (port 25)
eth1 = Inbound Interface
tcp = Protocol
destination = Direction of traffic
configure
edit nat destination rule 10
set destination address 1.1.1.1
set destination port 80
set protocol tcp
set translation address 10.0.0.5
set inbound-interface eth0
configure
edit nat destination rule 20
set destination address 1.1.1.1
set destination port 25
set protocol tcp
set translation address 10.0.0.10
set inbound-interface eth0
Using NAT with VPNs (NAT Exclusion):(NAT与VPN同时使用的情况处理)
As with typical VPN configurations, when you have a private-to-private (RFC1918) VPN tunnel between two networks, you will not want your NAT operations to translate your traffic destined for the remote network. To bypass NAT operations, we will use the SNAT example from above but include an exclusion for 172.16.10.0/24 traffic:
NOTE: Since we are configuring an exclude rule, we will need to give it a rule number lower than the default translate rule. This way, the exclusion will get matched before the translation rule.(因为我们正在配置一个排除规则,我们需要给该规则数值低于默认转换规则,这样处理之前的排除已有规则。)
configure
edit nat source rule 10
set destination address 172.16.10.0/24
set exclude
set outbound-interface eth0
edit nat source rule 20
set source address 192.168.148.0/22
set outbound-interface eth0
set translation address masquerade
Bidirectional(双向) NAT:
Bidirectional NAT is just a scenario where both SNAT and DNAT are configured at the same time. Bidirectional NAT is typically used when internal hosts need to initiate sessions with external hosts AND external hosts need to initiate sessions with internal hosts.(双向NAT适用于这样的场景,SNAT和DNAT都配置在同一时间。双向NAT时通常用于内部主机需要与外部主机发起会话和外部主机需要发起与内部主机的会话。即将内部主机映射到公网上。)
1.1.1.2 = SMTP Server (Public IP)
10.0.0.10 = SMTP Server (Private IP)
configure
edit nat source rule 5
set source address 10.0.0.10
set outbound-interface eth0
set translation address 1.1.1.2
edit nat destination rule 5
set destination address 1.1.1.2
set translation address 10.0.0.10
set inbound-interface eth0
Verifying NAT(验证NAT)
From the operational command prompt:
show nat [source | destination] rules
show nat [source | destination] translations
show nat [source | destination] statistics
clear nat [source | destination] counters
You can also verify NAT operations by viewing the sessions table on the vRouter. You can access the session table with the following command:
show conntrack table ipv4 [source <ip_addr> [destination <ip_addr>]]
Clearing session table entries:
delete conntrack table ipv4 [conn-id <connection_id> | source <ip_addr:port> [destination <ip_addr:port>]]
Logging NAT Rules(记录NAT规则)
You can enable logging for specific NAT rules within the command hierarchy. Remeber to only enable logging when needed and disable after you are done as it will flood the vRouter with unneeded log messages. You will need to issue the commit command for the changes to take effect.
To enable logging on a specific rule:
set nat destination rule 5 log enable
commit
To view or monitor active log messages (I use the run command because we are in configuration mode):
run monitor nat destination
To disable logging on a specific rule:
delete nat destination rule 5 log
commit
Sample Output:(输出示例)
Here you see an initial ICMP packet from the internal IP addres of 192.168.148.2 and destined for an external IP address of 4.2.2.2 being hit by the “source rule 10” NAT rule
vyatta@vyatta-test-1# set nat source rule 10 log enable
vyatta@vyatta-test-1# commit
vyatta@vyatta-test-1# run monitor nat source
NAT-SOURCE: [3832104.713106] [NAT-SRC-10-MASQ] IN= OUT=eth0 SRC=192.168.148.2 DST=4.2.2.2 LEN=84 TOS=0x00 PREC=0x00 TTL=63 ID=0 DF PROTO=ICMP TYPE=8 CODE=0 ID=59767 SEQ=1
vyatta@vyatta-test-1# delete nat source rule 10 log
vyatta@vyatta-test-1# commit
参考文档:
Brocade vRouter: Network Address Translation (NAT)
NOTE: Destination NAT happens first! Meaning that all firewall policies need to be written for POST DNAT operations.(DNAT最先发生,这意味着所有防火墙策略需要由DNAT处理后才可操作。)

它支持目前主流的三种NAT模式:Source NAT, Destination NAT, and Bi-Directional NAT (Both Source/Destination NAT),下列我们就开始了解它们吧。
There are a couple of points I would like to cover before going into the NAT configurations(在NAT配置中有如下一些要点):
1、Since NAT is a stateful operation, we do not need to configure bi-directional NAT for all configurations. The Brocade vRouter keeps track of the stateful NAT operations using the connection-tracking table.(NAT使用了状态表来跟踪维护此类包的的状态)
2、Unlike routing which will match the most specific entry, NAT operations are processed from top to bottom, with the first successful match used. All other NAT processing will be terminated at that point. Meaning it is important to number your NAT rules accordingly when planning your NAT scheme.(与路由相匹配的最具体的条目不同。NAT是从小到大的处理(规则号),如果最先匹配的那条符合规则的话,后面的规则将会终止处理,所以有必要規划好具体的逻辑并为之编号)
3、All NAT rules on the vRouter include the following parameters:
3.1、Defined traffic to be translated (filters)
3.2、The port-translation address (or the masquerade command if using the vRouter interface IP as the translated address)
3.3、The interface of which to apply the rule. Due to the nature in which the vRouter processes traffic, the translation type will determine the interface on which to apply the rule.
3.3.1、Source NAT – Applied on the outbound interface
3.3.2、Destination NAT – Applied on the inbound interface
4、The direction of the traffic. (Source, Destination, or both)
Source NAT (SNAT):
SNAT is the most common form of NAT. SNAT changes the source address of the packets traversing the vRouter. Typically used in a scenario where you need to translate the internal (RFC1918) addresses to a public routable address.(SNAT是最常见的NAT,SNAT瘵修改vRouter的包的源地址。最典型的场景是公司通过报号上网就是用的此类方式)
# 变量: 描述:
1、Rule Number Number of the SNAT rule. ules will be applied in numerical order.(以数字顺序编号的规则集)
2、Source Address Can be an IP or subnet of IPs.(源地址是ip地址段)
3、Translation Address Can be an IP Address. "masquerade" option uses the vRouter interface IP.(被转换为其它地址,masquerade为最常见)
4、Outbound Interface Interface that traffic will be egressing through.(定义要'出去'的网口)
Here a sample configuration of SNAT using 192.168.148.0/22 as the source, and the eth0 interface IP address as the translated IP:(以下示例用于将192.168.148.0/22这一段ip地址为源,将其转换通过eth0的ip地址出去)
configure
edit nat source rule 10
set source address 192.168.148.0/22
set outbound-interface eth0
set translation address masquerade
commit
save
exit
Destination NAT (DNAT):
DNAT changes the destination address of packets passing through the vRouter. DNAT is typically used when an external host needs to initiate a session with an internal (private) host. For example, translating a static public IP address to two internal server addresses, mapping them by a specific port. For our example, we will use the following parameters:(DNAT改变数据包的目的地址通过vRouter,DNAT时通常使用一个外部主机需要启动一个会话与内部(私有)主机。最常见的用法是将公网内部机器上的服务通过这种nat映射到公网上,让公司外部也可以访问内部这台机器上的服务,就好像这个服务就在公网的ip一样)
1.1.1.1 = Destination address
10.0.0.5 = Web Server (port 80)
10.0.0.10 = SMTP Server (port 25)
eth1 = Inbound Interface
tcp = Protocol
destination = Direction of traffic
configure
edit nat destination rule 10
set destination address 1.1.1.1
set destination port 80
set protocol tcp
set translation address 10.0.0.5
set inbound-interface eth0
configure
edit nat destination rule 20
set destination address 1.1.1.1
set destination port 25
set protocol tcp
set translation address 10.0.0.10
set inbound-interface eth0
Using NAT with VPNs (NAT Exclusion):(NAT与VPN同时使用的情况处理)
As with typical VPN configurations, when you have a private-to-private (RFC1918) VPN tunnel between two networks, you will not want your NAT operations to translate your traffic destined for the remote network. To bypass NAT operations, we will use the SNAT example from above but include an exclusion for 172.16.10.0/24 traffic:
NOTE: Since we are configuring an exclude rule, we will need to give it a rule number lower than the default translate rule. This way, the exclusion will get matched before the translation rule.(因为我们正在配置一个排除规则,我们需要给该规则数值低于默认转换规则,这样处理之前的排除已有规则。)
configure
edit nat source rule 10
set destination address 172.16.10.0/24
set exclude
set outbound-interface eth0
edit nat source rule 20
set source address 192.168.148.0/22
set outbound-interface eth0
set translation address masquerade
Bidirectional(双向) NAT:
Bidirectional NAT is just a scenario where both SNAT and DNAT are configured at the same time. Bidirectional NAT is typically used when internal hosts need to initiate sessions with external hosts AND external hosts need to initiate sessions with internal hosts.(双向NAT适用于这样的场景,SNAT和DNAT都配置在同一时间。双向NAT时通常用于内部主机需要与外部主机发起会话和外部主机需要发起与内部主机的会话。即将内部主机映射到公网上。)
1.1.1.2 = SMTP Server (Public IP)
10.0.0.10 = SMTP Server (Private IP)
configure
edit nat source rule 5
set source address 10.0.0.10
set outbound-interface eth0
set translation address 1.1.1.2
edit nat destination rule 5
set destination address 1.1.1.2
set translation address 10.0.0.10
set inbound-interface eth0
Verifying NAT(验证NAT)
From the operational command prompt:
show nat [source | destination] rules
show nat [source | destination] translations
show nat [source | destination] statistics
clear nat [source | destination] counters
You can also verify NAT operations by viewing the sessions table on the vRouter. You can access the session table with the following command:
show conntrack table ipv4 [source <ip_addr> [destination <ip_addr>]]
Clearing session table entries:
delete conntrack table ipv4 [conn-id <connection_id> | source <ip_addr:port> [destination <ip_addr:port>]]
Logging NAT Rules(记录NAT规则)
You can enable logging for specific NAT rules within the command hierarchy. Remeber to only enable logging when needed and disable after you are done as it will flood the vRouter with unneeded log messages. You will need to issue the commit command for the changes to take effect.
To enable logging on a specific rule:
set nat destination rule 5 log enable
commit
To view or monitor active log messages (I use the run command because we are in configuration mode):
run monitor nat destination
To disable logging on a specific rule:
delete nat destination rule 5 log
commit
Sample Output:(输出示例)
Here you see an initial ICMP packet from the internal IP addres of 192.168.148.2 and destined for an external IP address of 4.2.2.2 being hit by the “source rule 10” NAT rule
vyatta@vyatta-test-1# set nat source rule 10 log enable
vyatta@vyatta-test-1# commit
vyatta@vyatta-test-1# run monitor nat source
NAT-SOURCE: [3832104.713106] [NAT-SRC-10-MASQ] IN= OUT=eth0 SRC=192.168.148.2 DST=4.2.2.2 LEN=84 TOS=0x00 PREC=0x00 TTL=63 ID=0 DF PROTO=ICMP TYPE=8 CODE=0 ID=59767 SEQ=1
vyatta@vyatta-test-1# delete nat source rule 10 log
vyatta@vyatta-test-1# commit
参考文档:
Brocade vRouter: Network Address Translation (NAT)
